Intro
Discover 5 ways a Deacertificate enhances cybersecurity, ensuring secure data transmission with encryption, authentication, and trust, utilizing digital certificates and SSL.
The importance of understanding and utilizing Deacertificate cannot be overstated, as it plays a pivotal role in ensuring the authenticity and security of digital communications and transactions. In today's digital age, where data breaches and cyber attacks are increasingly common, having a robust system in place to verify the identity of entities and protect data integrity is crucial. Deacertificate, in this context, serves as a critical component, enabling secure and trustworthy interactions over the internet. This article aims to delve into the concept of Deacertificate, exploring its significance, applications, and the ways it contributes to a safer digital environment.
As we navigate the complexities of the digital world, it becomes apparent that security and trust are foundational elements. Deacertificate is at the forefront of this effort, providing a mechanism through which entities can be authenticated and data can be encrypted, thereby safeguarding against unauthorized access and tampering. The implications of this are far-reaching, affecting everything from financial transactions and personal data protection to the security of communication networks and the integrity of software applications.
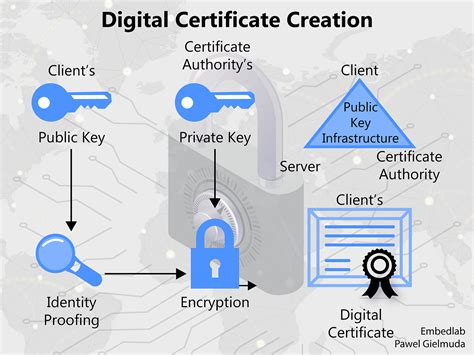
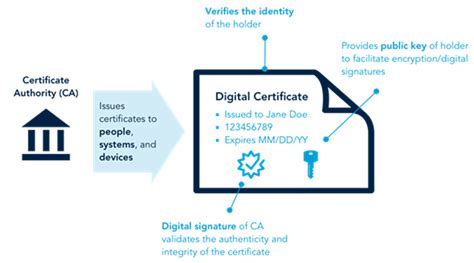
The concept of Deacertificate is deeply intertwined with public key infrastructure (PKI), a system that enables the secure exchange of data over the internet through the use of public and private keys. This infrastructure relies on certificates to verify the identity of entities (such as individuals, organizations, or devices) and to ensure that data is transmitted securely. Deacertificate, in this framework, acts as a digital certificate issued by a trusted certificate authority (CA), confirming the identity of an entity and its public key, thus facilitating secure communication and data protection.
Introduction to Deacertificate
Understanding Deacertificate requires a basic grasp of how digital certificates work and their role in public key cryptography. Essentially, a digital certificate is an electronic document that uses a digital signature to bind a public key with an identity — of a person, organization, or computer. This binding is asserted by a trusted third party, known as a Certificate Authority (CA), which verifies the identity of the entity to which the certificate is issued. Deacertificate, therefore, represents a specific type of digital certificate that is used for the purpose of decryption, allowing the holder to access encrypted data.
Benefits of Deacertificate

The benefits of utilizing Deacertificate are multifaceted, contributing significantly to the security and integrity of digital communications. Some of the key advantages include:
- Enhanced Security: By facilitating the secure encryption and decryption of data, Deacertificate plays a crucial role in protecting against unauthorized access and data breaches.
- Identity Verification: It ensures that entities are who they claim to be, reducing the risk of impersonation and fraud.
- Data Integrity: Deacertificate helps in maintaining the integrity of data by ensuring that any tampering or alteration during transmission can be detected.
- Compliance: In many industries, the use of digital certificates like Deacertificate is mandated by regulatory standards, ensuring compliance with legal and industry requirements.
Working Mechanism of Deacertificate

The working mechanism of Deacertificate involves several steps, including:
- Certificate Issuance: A Certificate Authority (CA) issues a Deacertificate after verifying the identity of the requesting entity.
- Key Generation: The entity generates a pair of keys - a public key and a private key.
- Certificate Signing: The CA signs the certificate with its private key, which can be verified by the CA's public key.
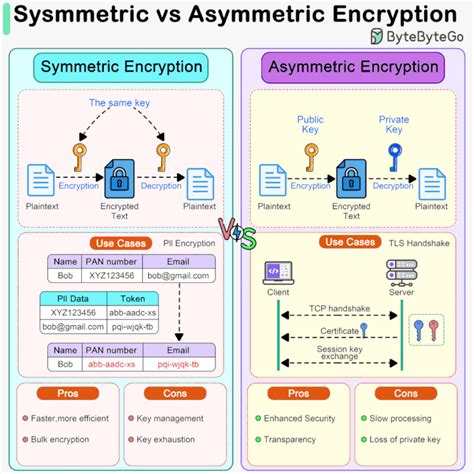
- Encryption and Decryption: The public key in the Deacertificate is used for encryption, while the corresponding private key is used for decryption.
Applications of Deacertificate

Deacertificate finds its applications in various domains, including:
- Secure Web Browsing: Ensuring that the website being visited is genuine and the data exchanged is encrypted.
- Email Security: Protecting email communications from interception and tampering.
- Virtual Private Networks (VPNs): Securing internet connections and protecting data transmitted over public networks.
- Software Code Signing: Verifying the authenticity of software and ensuring that it has not been tampered with during download.
Steps to Obtain a Deacertificate

Obtaining a Deacertificate involves the following steps:
- Generate a Certificate Signing Request (CSR): This is typically done on the server where the certificate will be installed.
- Submit the CSR to a CA: The CA will verify the identity of the entity requesting the certificate.
- Receive and Install the Deacertificate: Once the verification process is complete, the CA issues the Deacertificate, which is then installed on the server.
Gallery of Deacertificate Related Images
Deacertificate Image Gallery






What is Deacertificate used for?
+Deacertificate is used for the decryption of data, facilitating secure communication and transactions over the internet.
How does Deacertificate ensure security?
+Deacertificate ensures security by verifying the identity of entities and encrypting data, thereby protecting against unauthorized access and tampering.
What are the benefits of using Deacertificate?
+The benefits include enhanced security, identity verification, data integrity, and compliance with regulatory standards.
In conclusion, Deacertificate plays a vital role in the digital landscape, offering a robust mechanism for secure data encryption and decryption, and thereby facilitating trustworthy interactions over the internet. Its significance extends across various domains, from secure web browsing and email security to software code signing and VPNs. As the digital world continues to evolve, the importance of Deacertificate and similar technologies will only continue to grow, underscoring the need for heightened awareness and understanding of these critical security measures. We invite readers to share their thoughts and experiences with Deacertificate, and to explore further the vast potential it holds for enhancing digital security and trust.
